A New Level of Threat Complexity
The Simjacker vulnerability is currently being actively exploited by a specific private company that works with governments to monitor individuals. Simjacker and its associated exploits represent a huge leap in complexity and sophistication compared to attacks previously seen over mobile core networks.

The main Simjacker attack involves an SMS containing a specific type of spyware-like code being sent to a mobile phone, which then instructs the SIM Card within the phone to ‘take over’ the mobile phone to retrieve and perform sensitive commands.

The location information of thousands of devices was obtained over time without the knowledge or consent of the targeted mobile phone users.

During the attack, the user is completely unaware that they received the attack, that information was retrieved, and that it was successfully exfiltrated.
Example of how Simjacker can track mobile phone location of vulnerable subscribers
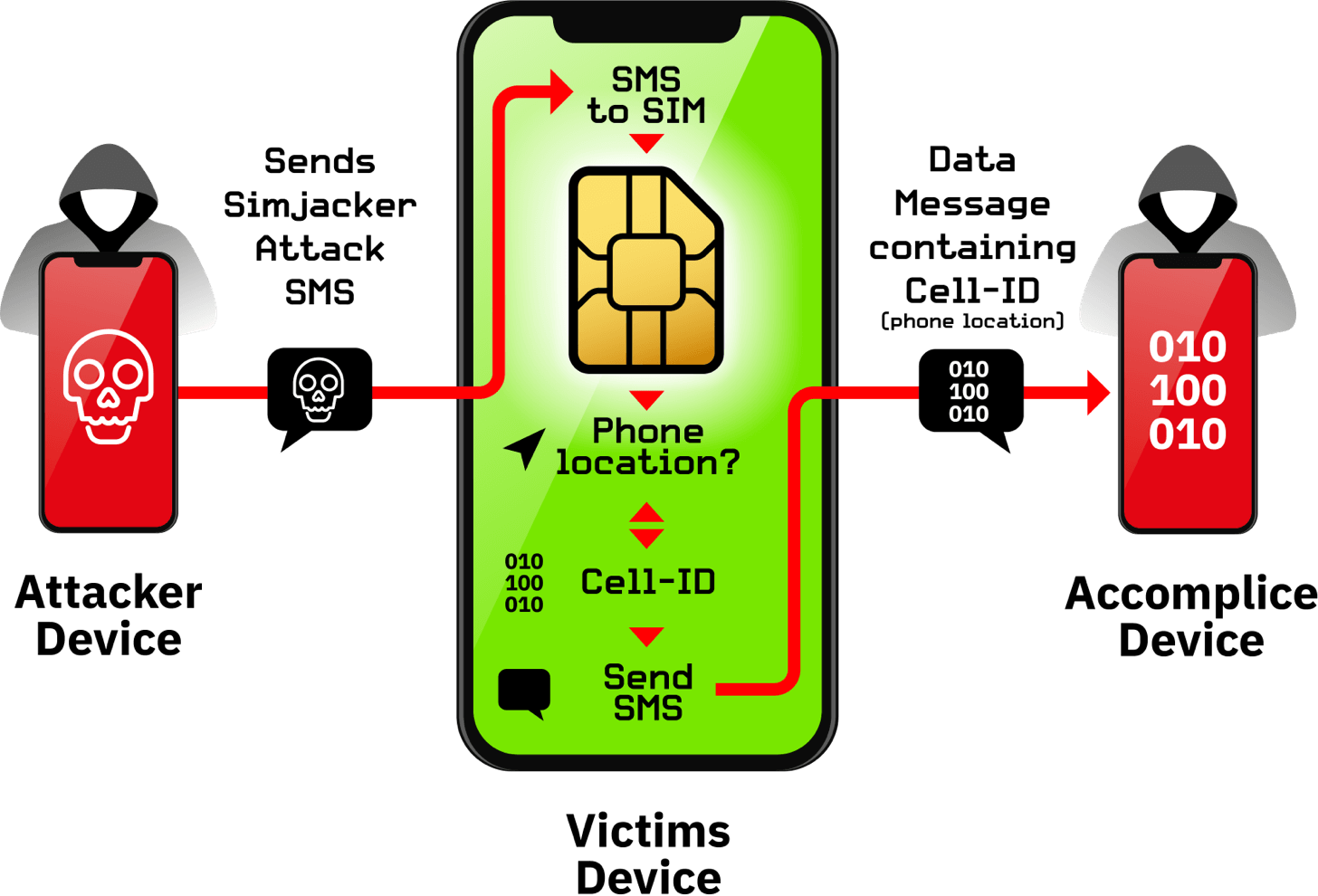
An attacker sends a Simjacker attack SMS from the attacker's device to the victim's device. In the victim's device, the SMS goes to the SIM card, instructing it to send an SMS with the phone's current cell ID to an accomplice device.
The Scale of the Simjacker Vulnerability and Attacks
Simjacker has been further exploited to perform many other types of attacks against individuals and mobile operators such as fraud, scam calls, information leakage, denial of service, and espionage. AdaptiveMobile Security Threat Intelligence analysts observed the hackers vary their attacks, testing many of these further exploits. In theory, all makes and models of mobile phones are open to attack as the vulnerability is linked to a technology embedded on SIM cards. The Simjacker vulnerability could extend to over 1 billion mobile phone users globally, potentially impacting countries in the Americas, West Africa, Europe, the Middle East, and indeed any region of the world where this SIM card technology is in use.
Stopping the attacks and building long-term defences
We are quite confident that this exploit has been developed by a specific private company that works with governments to monitor individuals. AdaptiveMobile Security has been working closely with their customers and the wider industry, including both mobile network operators and SIM card manufacturers, to protect mobile phone subscribers. We have blocked attacks and are committed to using our global threat intelligence to build defences against these new sophisticated attacks that are circumventing current security measures.
 Support Crack-Vault and help us keep providing free tools. Every donation counts!
(BTC) Address: bc1qhhva8uplmkaa3kkwxnux9t3y6l6kmhnwqzktzn
Support Crack-Vault and help us keep providing free tools. Every donation counts!
(BTC) Address: bc1qhhva8uplmkaa3kkwxnux9t3y6l6kmhnwqzktzn

 Support Crack-Vault and help us keep providing free tools. Every donation counts!
(BTC) Address: bc1qhhva8uplmkaa3kkwxnux9t3y6l6kmhnwqzktzn
Support Crack-Vault and help us keep providing free tools. Every donation counts!
(BTC) Address: bc1qhhva8uplmkaa3kkwxnux9t3y6l6kmhnwqzktzn