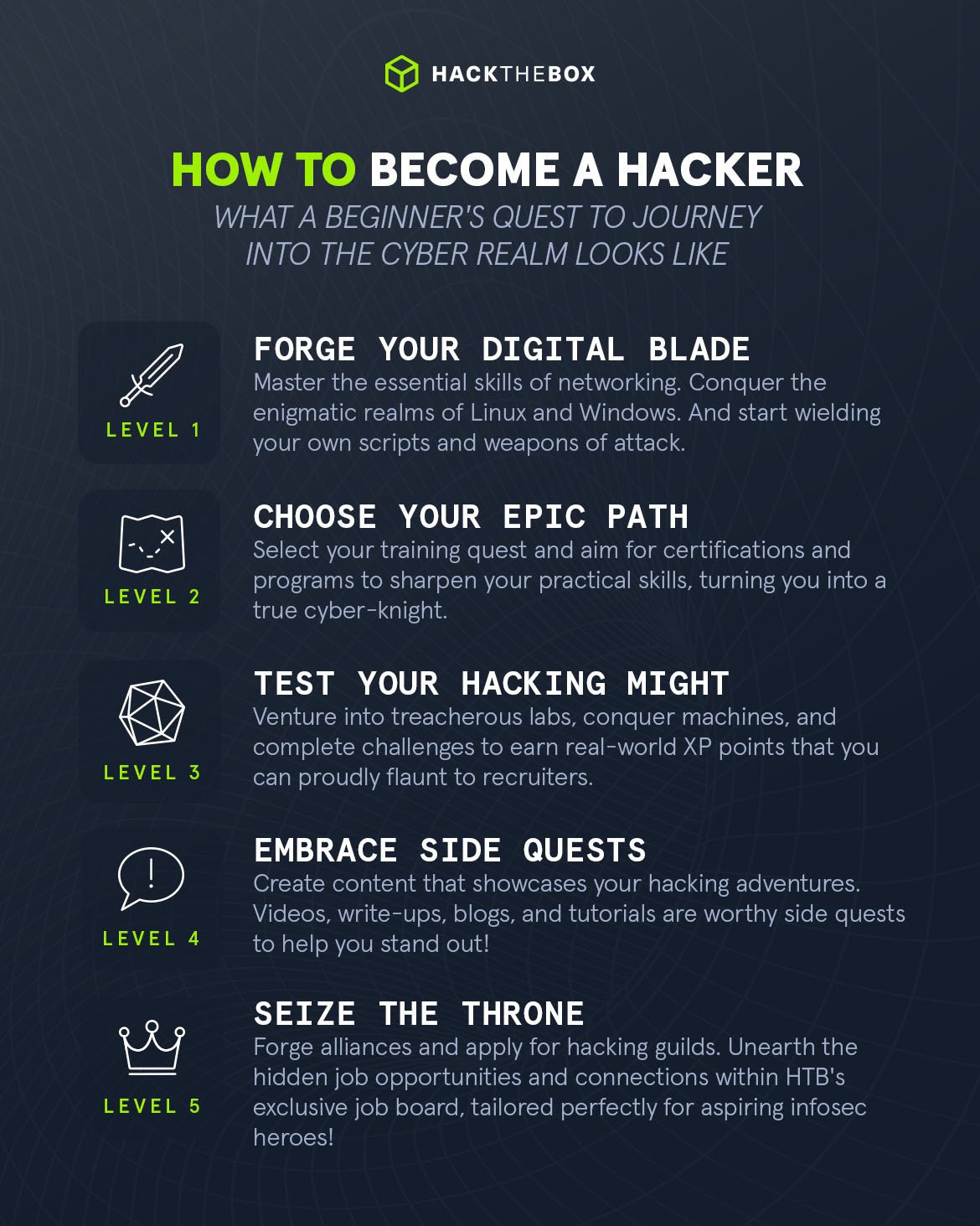
Hacking has come a long way from the days of simple brute-force attacks and basic phishing scams. In 2025, cybersecurity threats have become more sophisticated, leveraging AI, automation, and new vulnerabilities in emerging technologies. Whether you’re an ethical hacker, cybersecurity enthusiast, or just someone who wants to stay informed, understanding the latest hacking techniques is crucial.
- AI-Powered Cyber Attacks
Artificial Intelligence (AI) has revolutionized hacking. Cybercriminals now use AI-driven malware that can adapt and evade traditional detection mechanisms. AI-powered phishing emails can perfectly mimic human writing, making social engineering attacks more effective than ever. Meanwhile, deepfake technology is being weaponized to impersonate executives and politicians, leading to financial fraud and misinformation campaigns.
- Quantum Computing and Cryptography Threats
Quantum computing is still in its early stages, but researchers predict it could break traditional encryption methods within the next decade. Hackers and state-sponsored groups are already experimenting with quantum algorithms to decrypt sensitive information. The rise of quantum-resistant encryption is now a major priority for cybersecurity experts.
- Zero-Day Exploits on the Rise
Zero-day vulnerabilities—security flaws that have not been publicly disclosed or patched—are becoming more valuable than ever. Black market trading of these exploits has surged, with governments and cybercriminal groups paying top dollar for access. Ethical hackers (white-hats) and bug bounty programs play a crucial role in mitigating these threats, but the cat-and-mouse game between attackers and defenders continues to escalate.
- Supply Chain Attacks
Hackers no longer just target big corporations; they exploit smaller vendors and suppliers to infiltrate their main targets. By injecting malicious code into software updates or hardware components, they can compromise entire networks undetected. The SolarWinds attack was just the beginning—newer, more complex supply chain attacks have emerged, targeting cloud service providers and IoT manufacturers.
- Ransomware-as-a-Service (RaaS)
Ransomware attacks have become more accessible with the rise of Ransomware-as-a-Service (RaaS). Even script kiddies with minimal technical knowledge can purchase ransomware kits and launch devastating attacks. These ransomware operations have become more professional, offering customer service for victims to negotiate payments and even providing decryption keys after ransom is paid.
- IoT and Smart Device Exploits
With billions of IoT devices connected to the internet, security remains a major concern. Many smart devices have weak security settings, making them easy targets for botnets, data theft, and even physical attacks (e.g., hacking into smart door locks or surveillance cameras). Cybercriminals are increasingly focusing on IoT ecosystems, exploiting vulnerabilities to gain unauthorized access to networks.
- The Rise of Ethical Hacking and Bug Bounty Programs
On the brighter side, ethical hacking has gained immense popularity. Companies are actively hiring cybersecurity professionals to test their defenses, and bug bounty programs offer significant rewards for discovering vulnerabilities. Platforms like HackerOne and Bugcrowd have seen a surge in participants, proving that ethical hacking is a lucrative and respected career path.
 Support Crack-Vault and help us keep providing free tools. Every donation counts!
(BTC) Address: bc1qhhva8uplmkaa3kkwxnux9t3y6l6kmhnwqzktzn
Support Crack-Vault and help us keep providing free tools. Every donation counts!
(BTC) Address: bc1qhhva8uplmkaa3kkwxnux9t3y6l6kmhnwqzktzn

 Support Crack-Vault and help us keep providing free tools. Every donation counts!
(BTC) Address: bc1qhhva8uplmkaa3kkwxnux9t3y6l6kmhnwqzktzn
Support Crack-Vault and help us keep providing free tools. Every donation counts!
(BTC) Address: bc1qhhva8uplmkaa3kkwxnux9t3y6l6kmhnwqzktzn