Understanding DDoS Attacks: A Growing Cyber Threat
Introduction
In today’s interconnected world, cyber threats are evolving rapidly, and one of the most notorious among them is the Distributed Denial of Service (DDoS) attack. These attacks can cripple websites, disrupt online services, and cause massive financial and reputational damage to businesses and organizations. Whether you're a cybersecurity enthusiast, a business owner, or just an internet user, understanding DDoS attacks is crucial to staying protected.
What is a DDoS Attack?
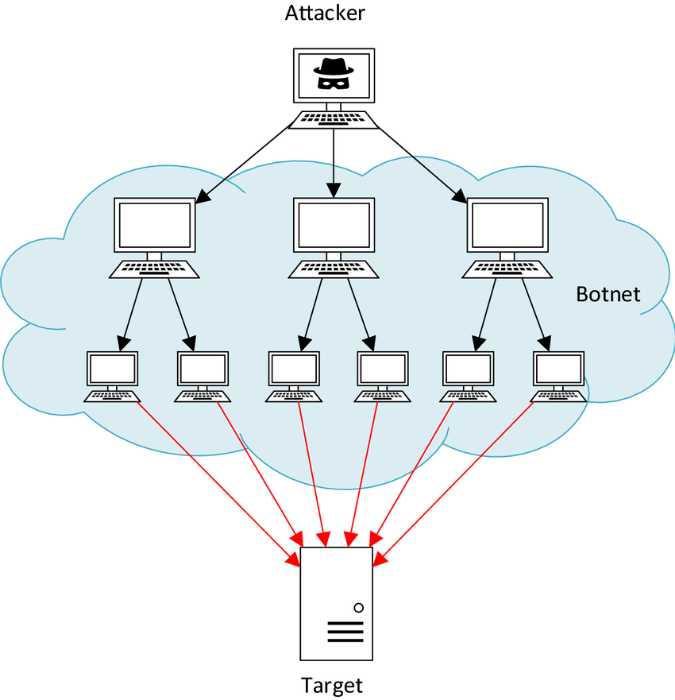
A DDoS attack occurs when multiple compromised systems, often part of a botnet, flood a target server, network, or website with an overwhelming amount of traffic. This overloads the system, making it inaccessible to legitimate users.
DDoS attacks are different from regular Denial of Service (DoS) attacks in that they use multiple sources (often globally distributed) to generate attack traffic, making mitigation much more challenging.
How DDoS Attacks Work
DDoS attacks exploit vulnerabilities in network protocols or flood servers with an excessive number of requests. Here’s how they typically unfold:
- Infection & Botnet Creation – Hackers infect vulnerable devices (PCs, IoT devices, routers) with malware, turning them into a botnet.
- Attack Execution – The hacker instructs the botnet to send an overwhelming amount of requests to the target.
- Service Disruption – The victim’s server or network becomes overwhelmed, causing legitimate users to experience slow or no access.
Common Types of DDoS Attacks
DDoS attacks come in various forms, each targeting different network layers:
1. Volume-Based Attacks
These attacks flood the target with a massive amount of traffic, consuming all available bandwidth. Examples include:
- UDP Flood
- ICMP (Ping) Flood
- SYN Flood
2. Protocol-Based Attacks
These exploit weaknesses in network protocols to exhaust server resources. Examples include:
- TCP SYN Flood
- Ping of Death
- Smurf Attack
3. Application Layer Attacks
These target the application layer (Layer 7 of the OSI model) by sending legitimate-looking requests that overwhelm web servers. Examples include:
- HTTP Flood
- Slowloris Attack
- DNS Query Flood
Why Are DDoS Attacks Dangerous?
- Financial Loss – Downtime can cost businesses thousands to millions of dollars.
- Reputational Damage – Users lose trust in a company that frequently faces service outages.
- Data Breach Risk – Some DDoS attacks serve as smokescreens for more serious breaches.
- Legal & Compliance Issues – Businesses may face penalties if attacks expose sensitive customer data.
How to Prevent and Mitigate DDoS Attacks
While no system is 100% immune, several steps can help mitigate the impact of DDoS attacks:
1. Implement Network Security Measures
- Use firewalls and intrusion detection systems to filter malicious traffic.
- Employ rate limiting to restrict excessive requests.
2. Use DDoS Protection Services
- Services like Cloudflare, AWS Shield, and Akamai offer DDoS mitigation solutions.
- Content Delivery Networks (CDNs) help distribute traffic, reducing the impact.
3. Monitor Network Traffic
- Anomaly detection tools can help identify unusual spikes in traffic.
- Set up automated alerts to respond quickly to potential attacks.
4. Strengthen Server Infrastructure
- Employ load balancing to distribute traffic efficiently.
- Optimize server performance to handle high traffic loads.
5. Educate Your Team
- Train employees on social engineering tactics used to initiate DDoS attacks.
- Keep systems updated with the latest security patches.
 Support Crack-Vault and help us keep providing free tools. Every donation counts!
(BTC) Address: bc1qhhva8uplmkaa3kkwxnux9t3y6l6kmhnwqzktzn
Support Crack-Vault and help us keep providing free tools. Every donation counts!
(BTC) Address: bc1qhhva8uplmkaa3kkwxnux9t3y6l6kmhnwqzktzn

 Support Crack-Vault and help us keep providing free tools. Every donation counts!
(BTC) Address: bc1qhhva8uplmkaa3kkwxnux9t3y6l6kmhnwqzktzn
Support Crack-Vault and help us keep providing free tools. Every donation counts!
(BTC) Address: bc1qhhva8uplmkaa3kkwxnux9t3y6l6kmhnwqzktzn