Introduction
Reverse engineering is a fascinating and essential skill in the world of cybersecurity, software development, and ethical hacking. It involves analyzing software or hardware to understand its design, functionality, and potential vulnerabilities. Whether you’re a cybersecurity enthusiast, a software engineer, or just someone curious about how things work, reverse engineering opens up a world of possibilities.
What is Reverse Engineering?
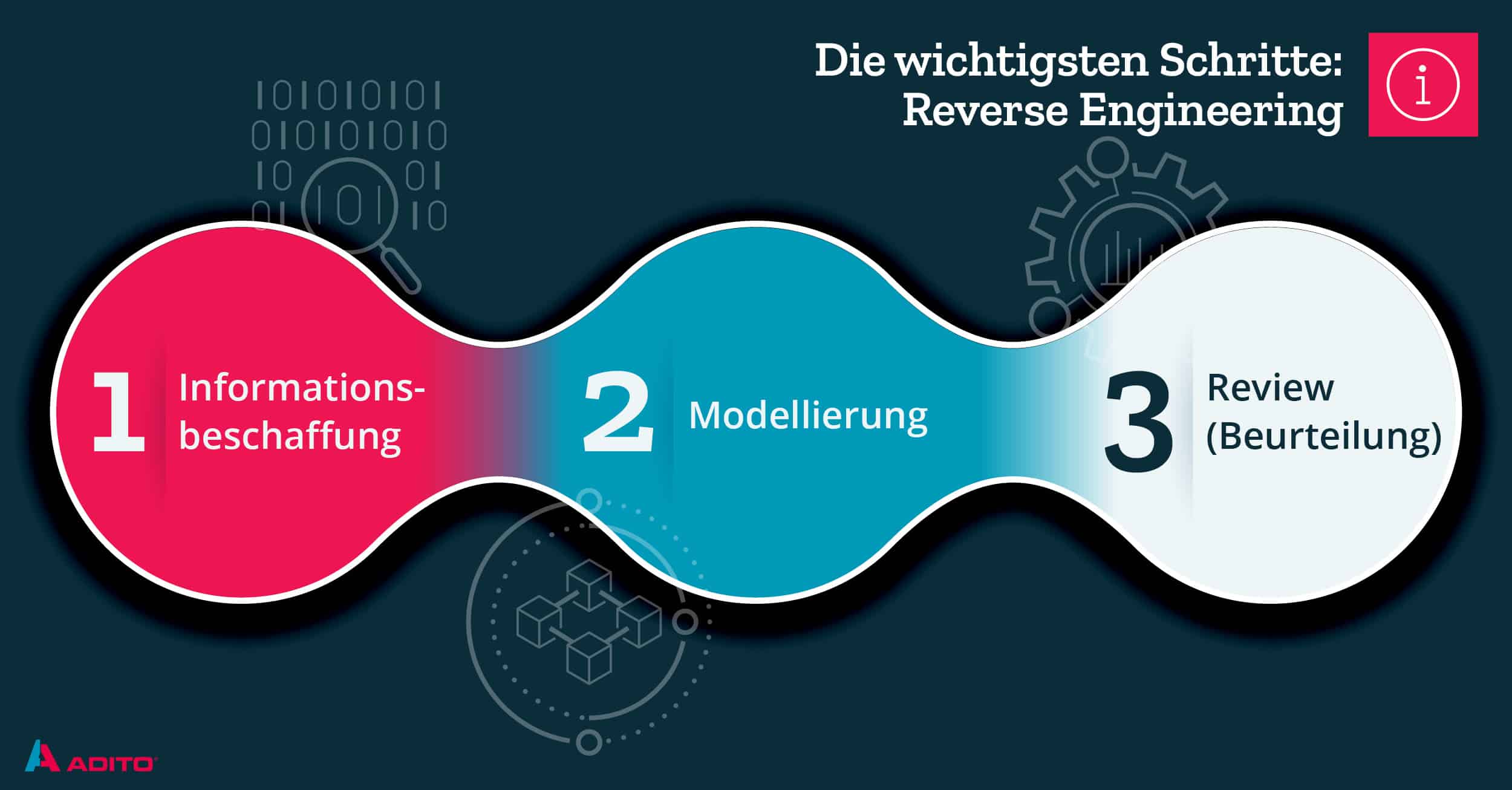
Reverse engineering (RE) is the process of deconstructing a system, software, or hardware to analyze its components, functionality, and behavior. It is often used to:
- Identify vulnerabilities in software and applications.
- Understand how a piece of software works without access to its source code.
- Recover lost or corrupted code.
- Improve software by understanding competitor products.
Tools Used in Reverse Engineering
Reverse engineering requires specialized tools that help analyze and dissect software or hardware. Some of the most commonly used tools include:
For Software Reverse Engineering:
- IDA Pro – A powerful disassembler and debugger.
- Ghidra – An open-source reverse engineering suite developed by the NSA.
- OllyDbg – A handy debugger for analyzing binary executables.
- Radare2 – A powerful framework for reverse engineering.
- Wireshark – A network protocol analyzer useful for analyzing communication between software components.
For Hardware Reverse Engineering:
- JTAG Debuggers – Used to analyze embedded systems.
- Oscilloscopes – Help in understanding electronic circuits.
- ChipWhisperer – A tool for analyzing side-channel attacks.
Applications of Reverse Engineering
Reverse engineering has several practical applications across different domains, including:
1. Cybersecurity & Ethical Hacking
Security professionals use reverse engineering to analyze malware, detect vulnerabilities, and strengthen security measures. Ethical hackers use it to find exploits in applications before malicious actors can take advantage of them.
2. Software Development & Debugging
Developers often reverse-engineer applications to understand how they function, especially when documentation is lacking. It also helps in debugging and optimizing software performance.
3. Malware Analysis
Reverse engineering is a crucial skill for cybersecurity researchers to dissect malware, understand its behavior, and develop countermeasures against cyber threats.
4. Intellectual Property Protection
Companies use reverse engineering to ensure their proprietary software or hardware isn’t being copied illegally or modified without authorization.
5. Gaming & Modding
Many gaming enthusiasts use reverse engineering to modify video games, create custom patches, and improve game performance.
Legal and Ethical Considerations
While reverse engineering is a powerful tool, it comes with legal and ethical concerns. Many software licenses explicitly prohibit reverse engineering. However, in some cases, such as security research or compatibility testing, it may be legally permitted. Always ensure you are complying with relevant laws and ethical guidelines when conducting reverse engineering activities.
How to Get Started with Reverse Engineering
If you’re interested in learning reverse engineering, here are some steps to help you get started:
- Learn Assembly Language – Since most reverse-engineered software involves analyzing machine code, understanding Assembly is crucial.
- Get Comfortable with Debugging – Practice using debuggers like Ghidra and IDA Pro.
- Analyze Open-Source Software – Reverse engineer open-source programs to understand their inner workings.
- Join Cybersecurity Communities – Forums and online communities can help you stay updated and exchange knowledge with experts.
- Practice on Capture The Flag (CTF) Challenges – Many cybersecurity competitions include reverse engineering challenges that help improve your skills.
 Support Crack-Vault and help us keep providing free tools. Every donation counts!
(BTC) Address: bc1qhhva8uplmkaa3kkwxnux9t3y6l6kmhnwqzktzn
Support Crack-Vault and help us keep providing free tools. Every donation counts!
(BTC) Address: bc1qhhva8uplmkaa3kkwxnux9t3y6l6kmhnwqzktzn

 Support Crack-Vault and help us keep providing free tools. Every donation counts!
(BTC) Address: bc1qhhva8uplmkaa3kkwxnux9t3y6l6kmhnwqzktzn
Support Crack-Vault and help us keep providing free tools. Every donation counts!
(BTC) Address: bc1qhhva8uplmkaa3kkwxnux9t3y6l6kmhnwqzktzn